This report is based on case study about company named Alron. The company is planning to expand their old, no more reliable wireless network to something better and secure where all employees will be able to share the information in securely. The original requirements of the company are to build computer network consisted on 10 computers. The report will include diagram how to design physical computer network. The resources as cabling, appropriate software, devices etcetera will also be explained in details.
A basic knowledge is required to understand building of computer networks and network security but in order to meet the report requirements appropriate terms will be still used. In this report will be discussed, how to build physical computer network with aid of diagrams and relevant examples to the original case study.
In the first section will be stated methods and tools how to build a computer network. Next stage is choosing appropriate software, but for this specific case we will choose a Windows server.
Follow stage will cover cabling and routing to our computer network. This section explains in deeper details, what devices are required to a particular computer network. TCP/IP explanations and examples will also be included. Network Security diagram and briefly explanation.
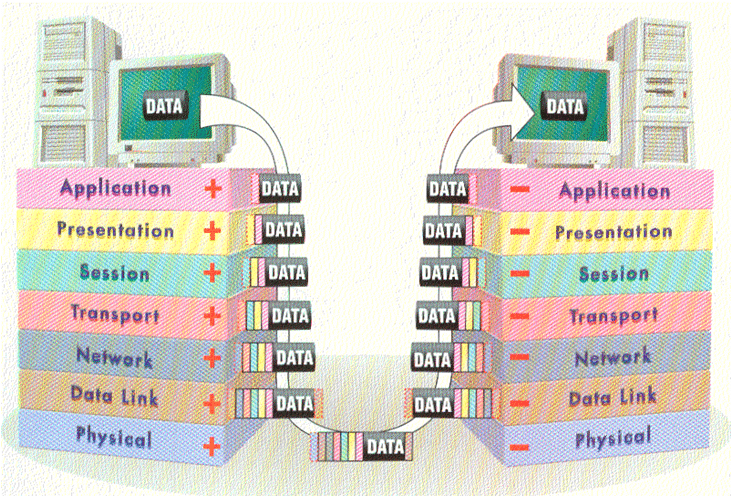
Clear full explanation to the seven OSI layers and the movement of data.
To design successful physical computer network for Arol, we have to choose from the varieties computer networks. As it was mentioned above we will concentrate to Client-Server. Particularly for this type of computer network it is very essential to know that some of the host are assigned to be servers. The server in this case provides certain resources. In this computer network we also have clients but, clients do not provide access of any network services. Servers also can provide shared storage or printers and the client will be assigned just for consuming these resources. In Arol some employees will have different privileges and for this purpose Client-Server is the best solution to secure files.
There are some advantages in this particular type of connecting the computers. The advantage is that clients could have different type of operation system.
And the other most important is if the network needs to be expanded further with Client-server this is very easy to achieve and cheap as well. When it comes for maintaining the servers this is very easy task. Maintaining in most of the cases include back up files with, Client-server it is necessary to back up one of the servers.
There are drawbacks as it comes, how much the company is ready to invest in their computer network. It is very essential fact simply why, every company tries to reduce their costs. In Arol the money are not problem and the company is ready to invest substantial amount of money. The reason is because are operating systems for servers are very expensive software. The other reason, which makes them so expensive, is because it requires significant time to design the computer network.
Physical movement of data
This section will focus exactly, on the action behind the scenes and along your network cabling. The OSI models has consistence of seven layers. Each layer has a purpose on the OSI layer model. Based on the diagram it will be easier to describe the magic of communication. Each Layer communicate it the layer above and below it.
Application layer
Application layer is the first stage where communicating is starting, this layer is responsible for determining when access to network resources is required. Application layer is leading to a small confusion because this term does not apply for the programs on the actual computer. For example, Microsoft Word or Power points are applications but they are not part of the OSI Models. The application layer networking software is responsible for delivering the request to the remote system. (Network Security Second edition chapter 3 page 38)
Presentation layer
Presentation layer is the layer, where the information is received or sent in appropriate format usable for the system applications. For example, if on this level the company Arol has to sends data to point (B) where point (B) is certain receiver. The data will be encrypted. However this is the main role of this layer encrypting and decryption the information usable for the application layer. Perfect example for this is the banks where they are sending valuable data via the internet. ( Network Security Second edition chapter 3 page 39)
Session layer
Session layer ensures that connection between two or more systems has been established successfully and their maintaining. It ensures that specific query for specific type of services is made correctly. The perfect example for this situation is, for example if the user is trying to access a system with web browser. Layers on the systems are working together to ensure you are receiving web pages not something else as E-mails. However the Session layer maintains unique conversation between the two or more systems. For example, user is trying to downloads two different web pages from two distinctive web sites in the same time on the same computer this, what actually the layer does is saving the information on the correct place and preventing mixing of information. To understand what is happening next we have to keep following the layers. Interesting thing is when we going one layer below we add one header a front of the present one as we can see clearly with the plus sings. (Network Security Second edition chapter 3 page 39)
Transport Layer
Transport Layer as it is clear from the name it is the layer which transports securely the data through the internet and prepare the files for delivery. Moreover the layer has specific purpose. Some of them are if the data is too large, the package is broken down to smaller files and numbered. This sequence of numbers helps on the other the transport layer to the other system to assemble everything to the original format.
Network Layer
Network Layer deals hoe the different systems find each other weather this is a name or number assigned to the network. Routers are getting into this layer and this is step before the connection with the internet.
Data Link Layer
Data Link Layer In this layer the both systems have established communication. The perfect example is Ethernet. Switches and Bridges are considered as “gate between the worlds”.
Physical Layer
Physical Layer The information already is transformed into a signal pulses and ready to be sent. Repeater and hub are example for device form this particular layer. The difference is that the repeater captures the signal and returns it back to its original strength and transmits it. (Network Security Second edition chapter 3 page 38)
This revising of the structure of the seven OSI layers helps us understand the basic function of each layer and its purpose. We can clearly notice that starting from the sender to the receiver we add one header a front of the follow one as it is shown on the diagram above. Then when the data has been successfully formatted and packed. The data is already to the Physical layer to the receiver we simply remove one of the headers of the previous layer.
Network Security
As the company Alron will have business operations activities they require highly network security model. Windows server provides these types of options which are suitable for the company as we can see on the diagram the company’s servers will be running on Windows server.
Network security provides five services some of these services are closely related with massage exchange using the network. To bring clear picture see the diagram.
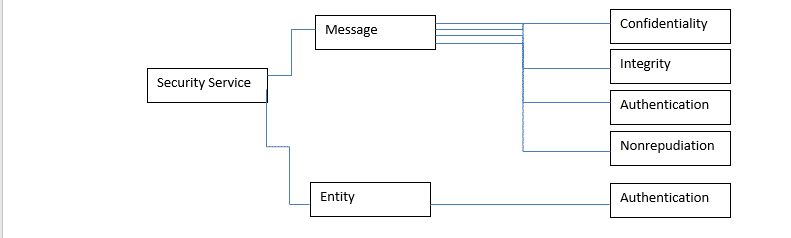
The message confidentiality is a very important bit of the network security. This means that the sender and receiver are expect privacy. This is the section where the message is encrypted and the message makes sense only for the receiver. For every other participant the message makes no sense.
Message integrity simply this message means that the data must arrive exactly to the receiver, where the message was sent to.
Authentication this is just security check process, where the receiver needs to be sure that the sender is the person who he presents himself.
Non-repudiation is the part where the all senders have not got the right to deny a sending message. This is used when a costumer put order to the bank to transfer money from Account (A) to account (B). In this matter the bank needs to be sure that this is actual request.
Authentication is simply just verification where the costumer or the user have right to access the system, complete operations, manage files.(Computer Networks 5-th edition Andrew S Tanebaum page784)
User accounts
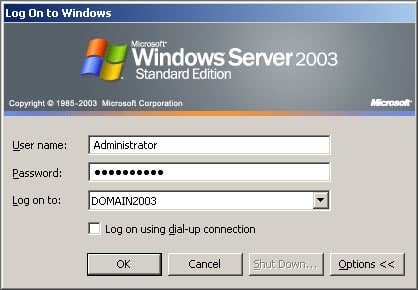
In computer network system user accounts can be created. Each of these users requires active directory user account to be able to log on and log off on computer or domain.
Each of these user accounts can be assigned with specific access to the data base. Every user could be assigned to a user group. This particular group has a limited access to the computer system. Individual users can be logged on to the computer system the same apply for user assigned to group.
This is one perfect example how Arol will be able to control their employees. Every employer will be able to assign remotely on every location on the world if needed.
This flexibility will be available thanks to the web Server, which you can see on the diagram. This server has RPS devise and can be shut down and activated remotely through the internet or with phone call.
Groups
There are 3 types of groups Local, Global, Universal. Each of these groups has its own roles for accessing and managing. Each of these groups has advantages and disadvantages but in this report we will not go into deep explanation about the group functions and their managing.
Domain
This is part of the Active directory and includes forest, domains or tree. Domain is actually group of computers and possibly other resources, which are part of windows Server 2003.
Hardware
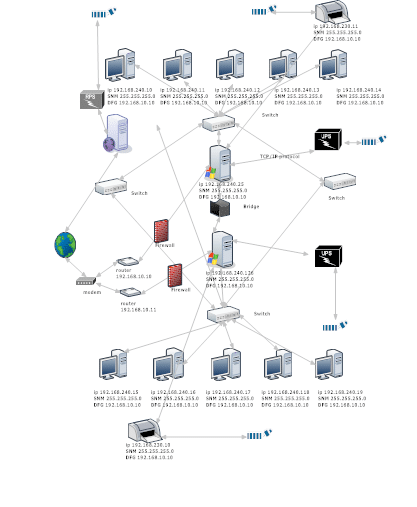
Computer Network Diagram
This computer network was design for to resist on variety of hardware failures. The constancy of this network has three servers. The first two servers which you can see on the diagram are running Windows server. There is web server which provides employees a big flexibility, which includes managing, operating database.
The first five computers separated with bridge which makes, the rest five computers absolutely independent. Cabling used is CAT 5.
The advantages of having one web server and two static servers are it give the company and employees a huge flexibility, preventing losing of data, faster work, in appearance of failure the system will be still running, remote control.
There are four switches allocated on the diagram the reason why these switches are so many is because of safety option if two or more fail to work.
There two routers allocated exactly before/after the modem exactly the same reason if one of the routers fail to work the second one will provide the access to internet.
There are two printers if one of the printers stop working the second one will do the work on the first one. The second advantage will be waiting tasks for printing will be dramatically reduced.
There are two UPS units in case electrical shock hit the servers. The advantage of having UPS unit is a big it safes the server to be damaged and sometimes it might takes months to back up the entire information. As we can see there is RPS unit which allows to shuts down or activates the server when it is needed. It could be done by phone call or through the internet.
And finally but not less important one modem, which is step before the accessing internet. The only disadvantages of having so complicated compilation of devises are it is too expensive and very hard for maintaining. But there is one more positive side the system can handle more than 200 computers.
Conclusion
Nowadays the technology allows a big variety of options of building a computer network. There is a huge range of software and hardware as well. But the reason why this particular system is running on Windows server is because is one of the most common. The security is very stable and the operating and managing is very reliable. Alron computer network is stable and flexible enough for the company’s requirements.
The report has approached the main fields of building and design computer network. The idea if this report was familiarizing of the main objectives of each of the designing process and the most suitable software.













